Hackers are trying more and more creative ways, but we can easily help ourselves with a little attention.
Nowadays, phone viruses are enjoying their peak again, sometimes masquerading as a courier tracking app, sometimes as a website that promises free prizes. For this reason, we can often not use some basic settings and options, which greatly reduces the chance of unauthorized access to our phones. With just a few small steps and a proper setup, we can help ourselves a lot, let’s talk about additional protection settings or just prepare for the worst case scenario.
Let’s see what small steps we can take to make things more difficult for hackers!
Passcode and other definitions
No matter how cool it sounds, many users don’t have a passcode or Face ID/Touch ID, so they can avoid the few tenths of a second needed to punch numbers or enter their fingerprints. However, this will be the primary line of defense for phones, which can be a great service not only in the virtual space, but also in the event of physical and physical theft.
to support
If we frequently backup our phones, we shouldn’t be surprised, no matter what situation we find ourselves in. It can also be useful if we can install some kind of malware, but it can also be useful in the case of lost and stolen phones. Most of the phone manufacturers also provide the ability to delete our mobile content remotely and if we have backups we can do it without data loss we can restore our previous and important data to the old or newly purchased device in seconds.
Do not store passwords on your phone
Many users type their passwords into the factory note-taking app, although a password manager built into the phone’s browser would be a more secure option. If you are looking for the ultimate in security, it may be worth looking into password manager apps (1Password, LastPass, etc.). These systems can usually handle multiple platforms at the same time, which can be a really useful feature if you have a Windows or Linux PC in addition to an iPhone and the Apple ecosystem option isn’t available.
Only from official places
This may be more important for Android users, but we can also find a workaround for iPhones these days. Download apps only from verified official websites, Play Store and App Store are our safest options in this regard. Some of the .apk and .ipa files circulating on the Internet are infected, and by installing them, we opened the way for unauthorized hackers to get into our phones. Of course, it may happen, for example in the case of Fortnite, that we have to download the application from the publisher’s website, but Epic Games or Blizzard will not deceive us.
Update, update, update!
Let’s try to keep both the phone’s operating system and our installed apps as up to date as possible. Older versions may contain vulnerabilities that make it easy for hackers. In the case of Apple iOS, several years of updates are guaranteed, but on the Android front, the situation is not as bad as before. Try to pay special attention to the apps too, it’s no coincidence that weekly updates arrive.
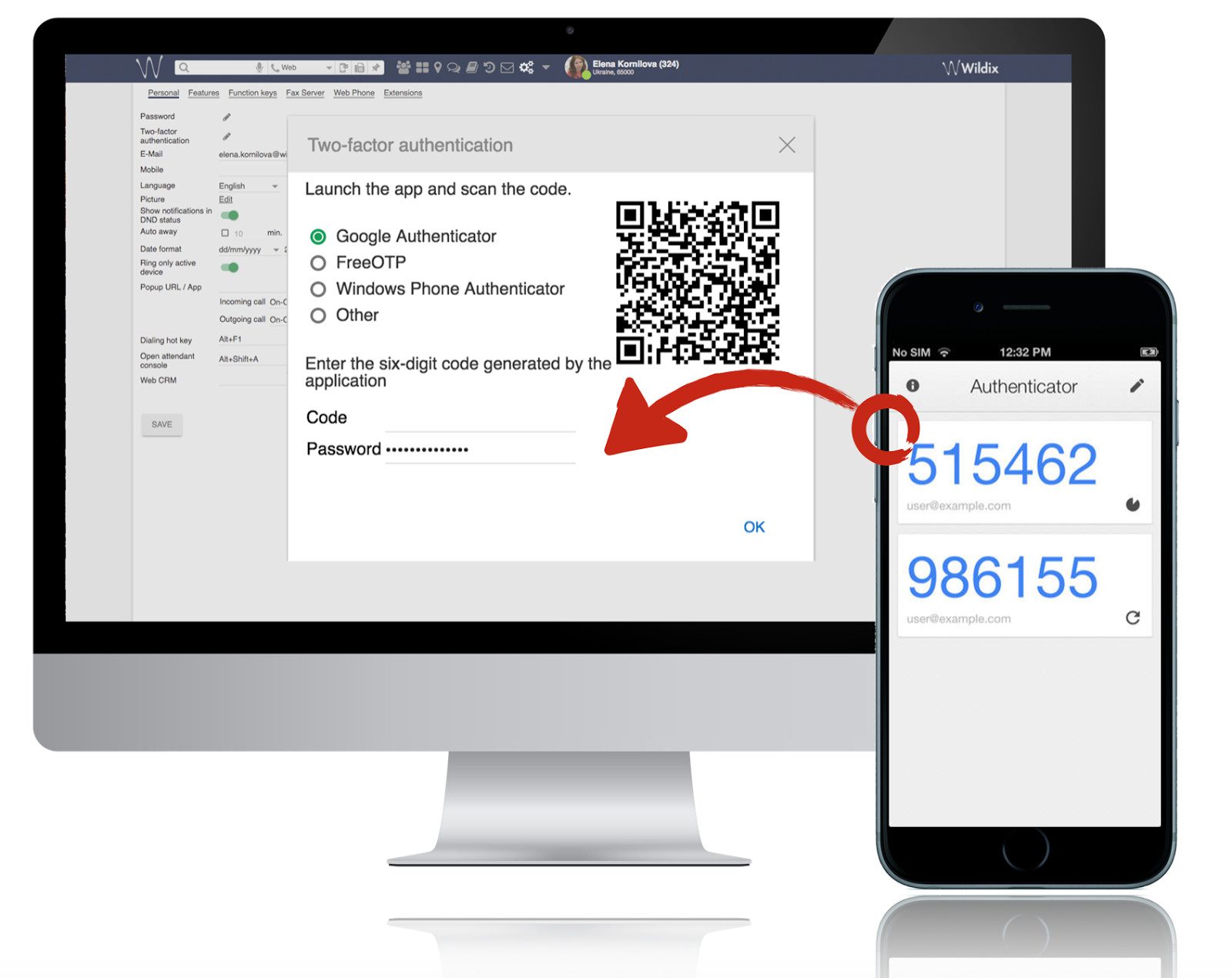
2FA
2FA, two-factor authentication, i.e. multi-step identification. Nowadays, it is requested by all service providers and websites, and not by chance. We don’t need to think of anything that requires additional knowledge, in fact, we need to verify ourselves in some other way in addition to the basic password. It can be a code copied from an additional email, SMS, or a string of numbers generated by a custom app. In fact, there are actually physical keys for those for whom security is the first thing.
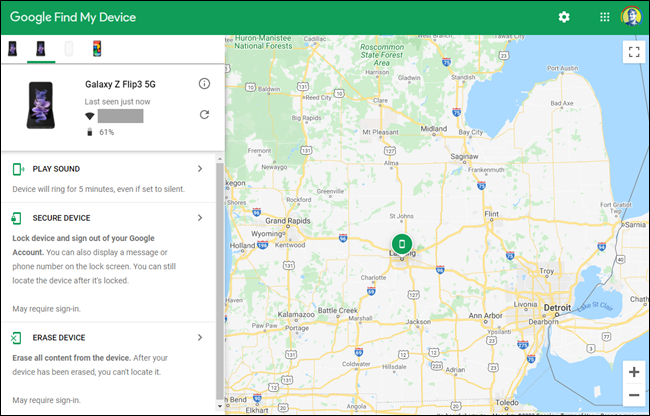
Prepare for the worst in advance
Unfortunately, even if you follow the above rules, your phone may be hacked or stolen. In this case, responding as quickly as possible can save us from our data falling into the wrong hands. It is worthwhile to study “in advance” the web interfaces provided by Apple, Google or the phone manufacturer, with which we can remotely monitor and even delete the contents of the phone. In the event of an emergency, we can take action in a few seconds on already familiar surfaces and do not have to rush nervously.
Are you doing everything you can to protect your phone?
source: PCWorld.com
Twitter likes this: Facebook and Instagram could really stop in Europe!